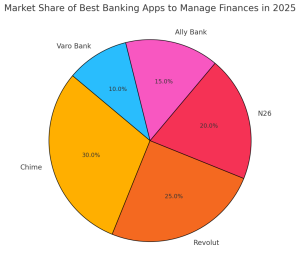
Introduction
In today’s fast‑paced development environments, reliable, repeatable, and scalable delivery pipelines are a must. GitHub Actions embeds CI/CD directly into your repository, removing friction between code changes and deployments. This guide covers everything from the core concepts and workflow anatomy, through build and test optimizations, to complex deployment strategies, secret management, notifications, and best practices. Whether you’re shipping a simple static site or orchestrating microservices in Kubernetes, you’ll walk away with a paste‑ready blueprint to automate builds and deploys end‑to‑end.

1. Core Concepts & Workflow Anatomy
| Term | Definition |
|---|---|
| Workflow | A YAML file in .github/workflows/ defining triggers and one or more jobs. |
| Job | A unit of work within a workflow, consisting of ordered steps and running on a runner. |
| Step | An individual task within a job—either an action or a shell command. |
| Action | Reusable code (Docker container or JavaScript) from Marketplace or your own repo. |
| Runner | The virtual or self‑hosted machine where jobs execute (e.g., ubuntu-latest). |
| Event | The trigger for a workflow, such as push, pull_request, workflow_dispatch, or schedule. |
Workflow Structure Example
yamlCopyEditname: CI/CD Pipeline
on:
push:
branches:
- main
pull_request:
branches:
- '**'
workflow_dispatch: {}
schedule:
- cron: '0 3 * * *' # nightly run
jobs:
build:
runs-on: ubuntu-latest
steps: [...]
test:
needs: build
runs-on: ubuntu-latest
steps: [...]
deploy:
needs: test
if: github.ref == 'refs/heads/main'
runs-on: ubuntu-latest
steps: [...]
2. Building Your Project
2.1 Language‑Agnostic Best Practices
- Checkout Early: Always begin with
actions/checkout@v3to pull your code. - Cache Dependencies: Speed up CI by caching language‑specific directories (
~/.npm,~/.cache/pip,~/.gradle). - Matrix Builds: Test multiple runtime versions, OSes, or configurations in parallel.
2.2 Node.js Example with Matrix & Caching
yamlCopyEditjobs:
build:
runs-on: ubuntu-latest
strategy:
matrix:
node-version: [14.x, 16.x, 18.x]
steps:
- uses: actions/checkout@v3
- name: Setup Node.js
uses: actions/setup-node@v3
with:
node-version: ${{ matrix.node-version }}
- name: Cache dependencies
uses: actions/cache@v3
with:
path: ~/.npm
key: ${{ runner.os }}-node-${{ matrix.node-version }}-${{ hashFiles('**/package-lock.json') }}
- name: Install dependencies
run: npm ci
- name: Lint code
run: npm run lint
- name: Run tests
run: npm test
- name: Build app
run: npm run build
- name: Upload build artifact
uses: actions/upload-artifact@v3
with:
name: app-build
path: build/
Key Benefits:
- Parallel coverage across Node versions
- Cache hits reduce install time by 60–80%
- Artifacts for downstream jobs (e.g., deployment)

3. Containerized Builds & Docker
| Step | Action |
|---|---|
| Checkout | actions/checkout@v3 |
| Build Image | docker build -t myapp:${{ github.sha }} . |
| Login to Registry | docker/login-action@v2 with secrets.GITHUB_TOKEN |
| Push Image | docker push ghcr.io/org/myapp:${{ github.sha }} |
| Scan Image | Use trivy or anchore/grype-action to catch vulnerabilities |
yamlCopyEditjobs:
docker-build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Build Docker image
run: docker build -t ghcr.io/myorg/myapp:${{ github.sha }} .
- name: Login to GitHub Container Registry
uses: docker/login-action@v2
with:
registry: ghcr.io
username: ${{ github.actor }}
password: ${{ secrets.GITHUB_TOKEN }}
- name: Push image
run: docker push ghcr.io/myorg/myapp:${{ github.sha }}
- name: Scan image for vulnerabilities
uses: aquasecurity/trivy-action@v0
with:
image-ref: ghcr.io/myorg/myapp:${{ github.sha }}
4. Deployment Strategies
| Strategy | Pros | Cons |
|---|---|---|
| SSH / SCP | Universally available, simple | Manual server config, less audit |
| Docker Container | Consistent environments, versioned images | Requires registry management |
| Cloud Provider CD | Native integration (EB, App Engine, AKS) | Vendor lock‑in, JSON/YAML config |
| Kubernetes (kubectl) | Declarative, scalable | Complex setup, RBAC and secrets |
4.1 SSH Deployment Example
yamlCopyEditjobs:
deploy-ssh:
needs: build
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: actions/download-artifact@v3
with:
name: app-build
path: ./build
- name: Archive build
run: tar czf app.tar.gz -C build .
- name: Copy to server
uses: appleboy/[email protected]
with:
host: ${{ secrets.SERVER_HOST }}
username: ${{ secrets.SERVER_USER }}
key: ${{ secrets.SSH_KEY }}
source: app.tar.gz
target: /var/www/myapp
- name: Deploy on server
uses: appleboy/[email protected]
with:
host: ${{ secrets.SERVER_HOST }}
username: ${{ secrets.SERVER_USER }}
key: ${{ secrets.SSH_KEY }}
script: |
cd /var/www/myapp
tar xzf app.tar.gz
systemctl restart myapp
4.2 AWS Elastic Beanstalk
yamlCopyEdit - name: Deploy to Elastic Beanstalk
uses: einaregilsson/beanstalk-deploy@v20
with:
aws_access_key: ${{ secrets.AWS_ACCESS_KEY_ID }}
aws_secret_key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}
application_name: my-app
environment_name: my-app-env
region: us-east-1
version_label: ${{ github.sha }}
bucket_name: my-eb-bucket
bucket_key: myapp-${{ github.sha }}.zip
4.3 Azure Web App
yamlCopyEdit - name: 'Deploy to Azure WebApp'
uses: azure/webapps-deploy@v2
with:
app-name: my-azure-app
slot-name: production
publish-profile: ${{ secrets.AZURE_WEBAPP_PUBLISH_PROFILE }}
package: ./build
4.4 Google App Engine
yamlCopyEdit - name: Deploy to App Engine
uses: google-github-actions/deploy-appengine@v0
with:
credentials: ${{ secrets.GCP_SA_KEY }}
project_id: my-gcp-project
deliverables: "./app.yaml,./build/**"
5. Managing Secrets & Configuration
- GitHub Secrets: Store credentials in Settings → Secrets → Actions.
- Environment Variables: Use
env:blocks orwith:in steps. - Encrypted Files: GPG‑encrypt complex configs and
gpg --decryptduring the workflow. - Least Privilege: Limit secrets’ scopes (e.g., read‑only tokens where possible).

yamlCopyEditenv:
NODE_ENV: production
API_URL: ${{ secrets.API_URL }}
DB_PASSWORD: ${{ secrets.DB_PASSWORD }}
6. Notifications, Approvals & Gates
6.1 Slack Notifications
yamlCopyEdit - name: Notify Slack
uses: 8398a7/action-slack@v3
if: always()
with:
status: ${{ job.status }}
fields: repo,commit,author
env:
SLACK_WEBHOOK_URL: ${{ secrets.SLACK_WEBHOOK_URL }}
6.2 Email Alerts
yamlCopyEdit - name: Send email
uses: dawidd6/action-send-mail@v3
if: failure()
with:
server_address: smtp.example.com
server_port: 587
username: ${{ secrets.SMTP_USER }}
password: ${{ secrets.SMTP_PASS }}
subject: "❌ Build Failed: ${{ github.repository }}"
to: [email protected]
body: "The CI build failed on commit ${{ github.sha }}."
6.3 Manual Approvals
Use workflow_dispatch with inputs, or introduce a manual approval step via environments:
yamlCopyEditjobs:
deploy:
needs: test
environment:
name: production
url: https://myapp.example.com
runs-on: ubuntu-latest
steps:
- run: echo "Deploying..."
GitHub enforces approval when the workflow targets a protected environment.
7. Advanced Patterns & Best Practices
- Reusable Workflows: Define common workflows in a central repo and call with
uses: org/repo/.github/workflows/ci.yml@v1. - Composite Actions: Bundle multi‑step logic into a single custom action to reduce duplication.
- Self‑Hosted Runners: Use for resource‑intensive tasks (game builds, large containers); manage autoscaling.
- Fail‑Fast: Run linters and unit tests before integration tests or deployment steps.
- Secrets Rotation: Automate credential rotation and audit via GitHub’s audit logs.
- Local Testing: Use
nektos/actto simulate Actions locally before pushing. - Workflow Documentation: Maintain a
WORKFLOWS.mdoutlining each pipeline, triggers, and key steps.

8. Monitoring & Metrics
- Workflow Duration: Track average job times; split long jobs into parallel steps if > 10 min.
- Runner Utilization: Monitor minutes used vs. available in your plan.
- Error Rates: Alert when > 5% of PR builds fail in a 24 h window.
- Deployment Success: Integrate post‑deploy smoke tests and rollback on failure.
Conclusion
GitHub Actions unifies your code, CI, and CD into a single source of truth. By leveraging matrix builds, caching, artifact passing, and first‑class support for secrets and environments, you can automate everything from linting and testing to multi‑cloud deployments and notifications. Adopting best practices—reusable workflows, fail‑fast logic, and robust monitoring—ensures your pipelines stay maintainable and performant as your codebase and team scale. Start crafting these workflows today to accelerate delivery, catch regressions early, and maintain rock‑solid confidence in every release.